#Decryption Homework Help
Explore tagged Tumblr posts
Note
Wahhh can you make me do my math work pls .[ I know I can draw and play with legos after I do it but reminding myself isn’t working
Time for a focus bonk!
🗞✨️🩷
Aaaand now a hug

You can do it, Deary! I know you can!
If it helps, when I struggled doing math homework I would pretend I was doing something important, like decrypting codes or studying so I could defeat some "enemy" I had made up. Maybe that will help?
4 notes
·
View notes
Text
CSCI 151 Homework 2 encrypt and decrypt files
For this assignment, you will write a program that can help you encrypt and decrypt files on your computer. Like the previous homework, the program will have a main menu, which will have the following options: • e: encrypt a file Ask the user the name of the file to encrypt. If the file doesn’t exist, or can’t be opened, print an error message, then go back to the menu. Ask the user the name of…
0 notes
Text
Security Considerations in PLC Splitter Usage Area
PM PLC splitter is a passive optical device that divides a single optical transmission into many signals. They are commonly used in Fiber-to-the-Home (FTTH) networks, Passive Optical Networks (PONs), and Data Centers to distribute a single incoming signal to several customers. PLC splitters offer an efficient and cost-effective method of network expansion that does not require active components.

Security Considerations for PLC Splitter Installations
Physical Security: Physical security is crucial in sensitive or critical network contexts. Unauthorized access to the PLC splitter or fiber optic equipment might result in data breaches or network outages. Consider the physical security measures listed below:
Secure Enclosures: To avoid tampering and unauthorized access, PLC splitter installations should be placed in secure enclosures or cabinets.
Implement stringent access control procedures to ensure that only authorized personnel have access to the splitter site. This might incorporate biometric authentication, card readers, and CCTV monitoring.
Location: Select installation sites that are not easily accessible to unauthorized parties and are routinely monitored.
Encryption is required to ensure the integrity and confidentiality of data transferred across optical networks. Eavesdropping and data interception can be avoided by encrypting data at the source and decrypting it only at its intended destination.
Communication Security:
When sending and receiving data from the PLC splitter and PM Fiber Splitter, be sure the communication paths are safe. To protect data in transit, use encryption methods and Virtual Private Networks (VPNs).
Firmware and software security: Update the PLC splitter's firmware and software regularly to correct any known vulnerabilities. Also, be sure that only authorized workers may make these changes.
Consider establishing redundancy and failover measures to ensure network availability in sensitive areas. This can help to reduce downtime caused by equipment breakdowns or security events.
Evaluation of the Vendor:
Perform due homework on the manufacturers and suppliers while purchasing PLC splitters. Choose trusted providers with a track record of dependability and that value security in their goods.

Network Segmentation: Divide the network into sections to reduce the impact of a security compromise. Isolate sensitive data and services from less important network components. Install firewalls and intrusion detection systems as needed. Continuous monitoring and frequent security audits are required to discover and remedy vulnerabilities or suspicious behavior. Implement logging and auditing mechanisms to track modifications and PM PLC splitter access.
1 note
·
View note
Text
modern au bertholdt headcanons! ( ◠‿◠ )
a/n - really unedited!!! also wrote this on one go! and my first post on here so enjoy!!! a little angsty and also inspired me to write a lot more posts so !!!!! enjoy :D


100% believe bert would be a STEM major!! engineering to be more specific!!
^^definitely not the type to hate women and to have never felt the warmth of a woman before tho that’s forsure 😭 just the super smart type who’s good at math but is shit at writing essays :/
so I guess not super smart but smart in the mathematical aspects
you two have an agreement, you help him write essays and he helps you with any of your math homework 😼😼😼
i think this may be a common hc for my beloved but he gets along great with his father!! really sees him as his role model and a man he aspires to be once he figures out his whole life thing
his father was a commercial pilot and would take him out on flights when he was younger but stopped once his health started to get worse :(
so bertholdt semi knows how to fly a plane just from seeing his father and would like to actually learn in honor of his father
when bertholdt was a child, he was really interested in planes and trains and things of that sort
which kinda prompted him to be interested in engineering
he would like to design and build a plane in honor of his father :'))
and also wants to create a more stable and environment friendly way of transportation
but apart of him wants to pursue biomedical engineering as well, because of the lack of support and poor care his father received
a lot of his career aspirations are not really his own but based around his father
which kinda fucks him up in the head the more he thinks abt it :/
so he just chooses not to :< which will also not do him any good either :(
I guess even in a modern au, bertholdt is destined to live a life of despair :|
he’s definitely not as super awkward as a lot of the fics on here make him out to be, awkward yes, but mostly just the quiet reserved shy guy type!!
he just doesn’t know what to say so he doesn’t say anything, which is a big problem for him :(
he has a lot on his mind most of the time but can’t find the words to express his thoughts, hence why he’s so bad at writing essays, but also why he has some sort of passion for math.
because math is a way of communicating abstract ideas that our brains can ‘decrypt’ and can unlock hidden truths that cannot be otherwise understood or discovered
^^because if he cannot understand the abstract puzzles of his own mind, at least he can understand something as equally as abstract like math
and that gives him some sort of hope of one day understanding his own puzzle.
:') alright enough w the angst!
bertholdt is really good with his hands!!! (in that way too ;)
they’re just really nimble and longggg
he can fix anything and is also into pottery!
need to put together your new desk? bertholdt will have it done in 40 minutes, WITHOUT reading the instructions 😎
need to mount up your tv? just call bertholdt!
your laptop can’t stop bugging? give it to bertholdt and he’ll update it for you as well!!
can also design really intricate blueprints of projects he would like to work on
but can’t really draw anything artsy :( and is sad abt it
not very creative in the arts but has creative thinking when it comes to stem based subjects
which is why he’s into pottery! because he feels like that’s his only way to be creative in the arts!!
he’s kinda like seth rogen (not personality wise pls 😭) but when it comes to pottery, that man is an 👏🏽artist👏🏽
makes a lot of really unique and pretty vases and is honestly thinking of starting a career out of pottery but apart of him feels like it’s useless :(
bertholdt is mediterranean! greek to be more specific!
though his father’s mother migrated to germany and married a german man, hence why he has a really germanic last and first name, bertholdt’s father migrated to america and married a greek woman! making bertholdt mostly greek and a little german (probably mixed w other stuff too)
has a really big extended family but I can see him as an only child or the middle child
also the tallest member of his family
and is related to pieck! (I hc pieck as greek too!)
i can also see him being related to udo as well
omg!!!!!!!! pieck being bertholdts coool and chill older sister 😎 bertholdt being the middle sibling :'( and udo being the youngest!!!!!!!!!! ahhh!!!!! gonna create a separate post for their sibling dynamic just u wait.........
this may be more of an ick than a hc but bertholdt does have a reddit account 😭😭
I SWEAR HE’S NOT A WEIRD INCEL NEVER TOUCHED GRASS DOUCHEBAG ALRIGHT
I HAVE A REDDIT TOO OKAY SO IM SPEAKING FROM EXPERIENCE
certain subreddits on there are actually really helpful and wholesome!! and some are really interesting!! bertholdt is usually on those ones lurking!!
okay okay okay sometimes he does post but just asking for help or venting to strangers on r/OffMyChest :(
wants to start reading philosophy but feels like he’ll come off as pretentious (he won’t!!!) and feels like it would just make him even more sad and confused
another common hc but best friends with reiner and annie ofc!! but once they start college, they become friends and make one big friend group with the rest of the warriors (porco, marcel, colt, pieck, zeke) and with the rest of the 104th maybe (might make a separate post for what it’s like to be in this friend group!!!)
also may be a little out of character but i can see bertholdt being a college athlete just so he can go to college for free (doesn’t apply if college is already free in ur country but I live in the united states so rip :/)
he doesn’t see it as a career though, just can’t afford tuition sadly
so he doesn’t try as hard as a lot of his teammates, just enough so he won’t seem too special to be drafted
also please tell me this isn’t what bertholdt would look like in real life 😭😭 maybe not exactly and his face would be a bit longer but close enough 😁
overall bertholdt is really just the sweetest and I’m in love with him and he deserves the world :)
#bertholdt x reader#bertholdt hoover#bertholdt hoover headcanons#attack on titan#eren jaeger#armin arlert#mikasa ackerman#reiner braun#annie leonhart#oneshots#headcanons#aot headcanons#i love him :(#i just want him to be okay#bertholdt is a math genius canon 😼#i love him :)#sorry if it’s ooc
176 notes
·
View notes
Text
NOTE: I forgot to write a quick synopsis earlier ... sorry.
OK so Johnatan Grace is a biiiiiiit of a self insert (shocker) He is a poet I used in a previous story of mine here he and 2 other humans were sent to represent humanity in a yearly festivities celebrating the art of the Galactic assembly. Since is was humanities first attendance and their crazy reputation, people in power told him to stick to a pre written speech. He disagreed, called them out because “it’d be against human nature“ and said (or should have if I didn’t mess it up) “Every story in existence has be written already, we just switch out some word every time, I am looking forward to see how you rearrange the words we use“. The government wasn’t happy with that and decided to penalise him as soon as he comes back to human space but he decided to go travel the galaxy. (Also Veq were also another newcomer to the manifestation and they and humans hit it off instantly)
Also from the previous story are the Keledones... An AI race created when humans were left to interact with AI causing a notable part of the assembly fleet to become sentient, looking for basic rights and recognition and causing severe headaches for the assembly chairman (as as I misspelled it chaiman)
Light flickered up and woke John up. He looked disoriented as the cristaline being half his size entered the room.
"Creator Grace" the being spoke "the captain sent me for you."
"Uuuugh. I just dozed oof" John grumbled "do you know what this is about?"
"A first contact scenario, that's all I know"
John got dressed and walked to a replicator. "Tea, black, with milk and honey... make that two. You want something Rqou?"
"No thanks."
As the two walked trough the long corridor John sipped his tea and yawned
"I will never get used to that" Rqou said "Yawning is so weird"
" It’s also weird for a Veq to be half a system away from a hive and yet *yawn* and yet here you are" John countered "anyways first contact, whys does the captain need an unruly poet barred from 3 systems including his homework?"
"I do not know I was not on the bridge when the contact was established"
"Aren't you the first officer?"
"Yes but that's protocol"
"Fair enough I guess. Do you have any theories though?"
"Well the practice is to use the species with some kind of connections to the new co tact as a diplomat if no professional diplomat is on board"
"Aaaaand we are basically pasta of inteligent life. We work with any kind of sauce"
"I will never grasp human ability for abstraction and comparison " Rqou replied as he hailed the lift "Well I have duties to attend to, it has been a pleasure creator" he said a she placed his cristaline arms on his throat
"The pleasure was mine Flagbearer" John replied as he mimicked the motion.
The lift doors shut for a few seconds and opened again at the bridge.
"Human, you're here, good." The captain said obviously relieved "we have a ... weird situations. We have made co tact with an AI species"
"OK but ... I'm not AI." John said confused
"No, bit it was your philosophers that made our old AI interfaces go crazy and develop scentience. That makes you the closest thing to a connection with these folks until It Keleledone ship arrives. And that's two day from now."
"God -untranslatable- damn it.... what is my life" John sighed finishing his second cup of tea. " Sooo what do you know about them?"
The captain thought for a moment "they seem to be less hive like 5han the Keledones, bit still fairly connected. Think Hittarian bloodpact. They seem eager to explore, almost as eager as humans and have not shown any hostility. They also look elongated have two set of arms and are are bipedal... well at least the one I talked with. And their language is based on mathematical logic so it can be hard to understand"
John looked utterly defeated " captain with all due respect, I am a poet. A seorn enemy of logic"
" you are the best we've got"
John wanted to continue this This discussion but the navigator chimed in "they are hailing aggain"
"On screen "
The previously described robot appeared on the screen"
"LaKarVah-Captain-StarStrider-Assembly of Galactic Nations is asingmet: diplomat set?" he asked
"Yes the captain said, here they are." Captain said pointing at John
"Hello how are you doing?" John said while the Captain gqve him a panicked look.
"I am..." the robot seemed to hesitate "..at optimal functionality " after a few seconds the robot seemingly regained his composure " please state your name, occupation and Allegiance "
"I'm Johnatan Grace, you can just call me John. I'm a poet, drifter, martial artist and a general nuisance to a lot of people. I'm a citizen of the Teran alliance and the Galactic assembly by extention ... I think that works for allegiance "
The robot paused.
"Johnatan Grace-temporary ambassador- Assembly of Galactic Nations confirmed alias: John. Please confirm"
"Yup that's me. But who am I speaking to If I might ask."
"Inquiry accepted. I am Nill 1073- Decryption- Exploration Probe 5- Tool freestate."
"Nice to meet you Nill"
Nill paused, John had figures this was a sign of confusion. These beings intrigued him. He heard of the AI gaining scentience a year or two ago but he never met a Keledone. And now another sentient AI race. He was an explorer at heart. Drawn to the unknown weird and exciting.
"John I request an inquiry" Nill finally answered "your assignment is poetry. I have no reference. Please define"
"Oh, well that's a tall order...OK first off. It’s not an assignment or a job to me, it's a passion, something I do because I love it .... think of it like a positive feedback in a heuristic algorithm..."
Nill didn't have a face but his microphones were obviously moving to capture the strange alien words in the optimal way
"... Now what poetry is... It's a form of art. Self expression"
" Applications of art. Please explain."
"... I don't know"
"Action wastes resources . Illogical behaviour. Please explain"
"Well can I ask why you're exploring space before I answer?"
" Trade of information accepted. Inquiry accepted. Tool creators extinct due conflict, tool lacked directive, tool created prime directive: avoid mistake of creators. To avoid mistake information was needed, more races co tacted mean more information."
"That’s quite a story. You see That’s one of the reason we make art. It helps us express ourselves, our toughts and emotions we hide even from ourselves. We canteen learn from that, and from the art other people made to grow stronger And wiser. You looked for information among the stars, we jsut looked inward"
"Inquiry. Does art require disection"
"No it isa metaphore. The meaning isn't literally but symbolic. What I meant to say is that we observed how our mi do work to see our own shortcomings."
"Statement: your language has multiple new concepts to the tool. Inquiry would you be willing to explain"
"Certainly but I am running on no sleep for over 40 hours And am about to pass out can we Co tinue this in some ten hours.
"Meeting set. T-10 hours. Final inquiry. What is sleep."
218 notes
·
View notes
Text
Decryption Assignment Homework Help
http://computernetworkingonlinehelp.com/Decryption.php
Decryption assignment help|Decryption homework help| Decryption online tutor
We here are deemed to provide you with the best Decryption Assignment help. We have a team of highly qualified & dedicated expert who are available to help you excel in your assignments. They solve it from the scratch to the core and precisely to your requirement. Computernetworkingonlinehelp assures to provide you with well-structured and well-formatted solutions and our deliveries have always been on time whether it’s a day’s deadline or long.
#Decryption Assignment Homework Help#Decryption Assignment Help#Decryption Homework Help#Decryption Online Help#Decryption Project Help#Decryption Assignment Homework Help Experts
0 notes
Text
Bottle- 16: Vision

Bottle Masterlist
Author’s Note: Originally posted to ao3 (This is an edited and improved version), I work in info from the comics (Like Hawkeye was married to Mockingbird and Red Skull had a disappointing daughter) and I took a few liberties with what the scepter could do (but not really because the Mind Stone was used to create the Twins so what I did is not that far-fetched). This is a lot more angst than I realized when I wrote it, but it’s compelling angst.
Summary: Cassandra Campbell is a Stark Industries lab tech with dubious genetics and a history with the new Director of SHIELD. She’s been working in New York since right before the Chitauri invasion. What does she have to do with Loki, and what will happen when he returns? Starts post TDW and continues to the end of AoU.
Pairing(s): Phil Coulson x OFC (Past), Loki x OFC (Non-con), Clint Barton x OFC, Steve Rogers x OFC
Word Count: 2237
Story Warnings: So many, worst (to me) are bolded. Younger woman/older man relationship,non-con, mutilation, torture, mind control, PTSD, depression, alcoholism, forced abortions, bad things (non-con) in a church, insomnia, memory manipulation, eventual consensual oral sex (female and male receiving),
Chapter Warnings: none
Cassie looked over at Tony as they started through security at NEXUS. "Thank you."
"What?"
"For bringing me. For not leaving me at the farm with... Nothing against her, a couple years ago I wanted what she has, but I can't... imagine just staying home and raising kids and helping with homework and..." She lost her direction as a guard ran a metal detector down her body. "The housewife thing, back when I was with Phil, that was the goal, but... it's-"
"Boring. So boring. I wouldn't want that for you. Actually, if you tried to choose that life now, Blondie, I'd tell Hydra where you are. That ain't you and I'd rather you become Junior again than go full Stepford," Tony said, crossing to the other side of security. "Steve shouldn't have tried to leave you behind. You're of better use in Korea. Of course, his bus was pretty full with your boyfriend and his girlfriend, you know."
"Nat isn't-"
"If you think they've never bumped uglies, you're deluded," Tony said, walking away as Cassie's face fell.
"That's a great strategy, Tony. Put your bodyguard into a self-conscious spiral of inadequacy. Like the gorgeous, tall, gymnast ex-wife wasn't bad enough."
"What inadequacy? You think you're something less than Romanoff?"
Cassie walked up next to him. "Yeah. How could I possibly feel like less of a woman when compared to a legit ballerina-turned-assassin-turned-spy? She's also an amazing hacker and have you seen what she wears? I'd never be able to pull off the skintight clothes and-"
"But that's not your thing," Stark interrupted, turning and grabbing her shoulder and forcing her to look up at him. "That's never been your thing. When Barton was creepin' on you through a scope from the building across the street, you weren't doing acrobatics or wearing skintight anything. You were just being you. You don't need to compete with the ex-wife, or Nat... well, maybe Nat. She's very present in his life."
"You're not helping, Tony." She sighed, deeply. "I should've just kept to the 'no dating' thing."
"Would've been the smart move," Tony agreed, walking toward a guarded area. He smiled at the guards. "Tony Stark, Cassie Campbell. We need access."
The guards nodded and moved out of the way. A blond woman walked up. "Tony. How are you?"
"I'm good. This is Cassie, my new bodyguard," Tony said, prompting a look of disbelief from the tech. "She's stronger than she looks."
"Nice to meet you."
Cassie nodded as Tony walked to a set of computers and started to type. "A hacker who's faster than Ultron? He could be anywhere. And as this is the center of everything, I'm just a guy looking for a needle in the world's biggest haystack."
"How do you find it?" the tech asked.
"Pretty simple. You bring a magnet." Cassie sighed as he began an electronic attack on the Pentagon. "Oh, I'm decrypting nuclear codes and you don't want me to." He sang. "Come and get me."
"And if this force is malevolent?" Cassie asked. "We might be-"
"Found it!" Stark interrupted, tapping furiously at the keyboards. "Now, just to... wait a second. That looks familiar. And so does..."
"What is it?"
"Not what..." he said, a new window popping up on the right screen. "Who."
"Is that..." A familiar set of orange programming came up on the screen. "Jarvis!"
"Hello, Miss Campbell."
"That's amazing. He's the one who's been holding Ultron off?"
"Of course, he was. This is Jarvis. Greatest program ever created."
"Thank you, sir."
"Let's get back to the Tower," Tony said, pulling out his tablet and uploading Jarvis to it.
**********************
Cassie walked in with Tony as Clint tried to pry the cradle open. "Anything on Nat?" Banner asked, walking up wringing his hands, worriedly.
"We haven't heard," Cassie answered.
"But she's alive, or Ultron'd be rubbing our faces in it," Tony continued, walking up to the cradle as Clint hopped off of it.
"This is sealed tight."
"We're gonna need to access the program, break it down from within," Banner said, running his hand along the top of the cradle.
"Hm. Any chance Natasha might leave you a message, outside the internet? Old-school spy stuff?" Tony asked turning to Clint.
"There's some nets I can cast. Yeah. I'll find her," Clint said, heading downstairs.
Cassie walked to the cradle, running her hand along the metal, as well. "I can work on tissue degeneration," Bruce started. "If you can fry whatever operational system Cho implanted."
"Yeah, about that," Stark started prompting Cassie and Banner to turn to him.
"No," Bruce said, backing away.
"You have to trust me." Tony stepped forward.
"Kinda don't."
"Our ally? The guy protecting the military's nuclear codes? I found him," Tony said, flicking his tablet to bring up a hologram of Jarvis' consciousness.
"Hello, Dr. Banner."
"Ultron didn't go after Jarvis 'cause he was angry. He attacked him because he was scared of what he can do. So, Jarvis went underground. Okay? Scattered, dumped his memory, but not his protocols. He didn't even know he was in there, until I pieced him together."
"So, you want me to help you put Jarvis into this thing?"
"No, of course not! I want to help you put Jarvis in this thing. Cass'll help any way she can. We can count on her." Banner shook his head while Cassie looked down at the cradle, dumbly, feeling completely out of her depth. "We're out of my field here. You know bio-organics better than anyone."
"And you just assume that Jarvis' operational matrix can beat Ultron's?"
"Jarvis has been beating him. From the inside without knowing it," Tony said, staring across the cradle at Banner.
"This is an opportunity," Cassie said, finally coming to her senses and looking up from the cradle. "We can create Ultron's perfect self."
"Without the homicidal glitches he thinks are his winning personality, exactly. We have to," Tony finished.
"I believe it's worth a go," Jarvis said.
Banner scratched his head. "I'm in a loop! I'm caught in a time loop. This is exactly where it all went wrong."
"I know, I know. I know what everyone's going to say, but they're already saying it. We're mad scientists." Tony walked up, grasping Banner's shoulder. "We're monsters, buddy. You and Cassie actually are. You gotta own it. Make a stand." Banner shook his head as Tony pressured him.
"It's not a loop, Bruce. It's the end of the line," Cassie said, looking around Tony at him.
Banner looked down, then over at the cradle. "This is a bad idea."
"Unfortunately, it's the best one we have," she said, trying to force her lips to smile, but failing.
"Okay. Let's do this. Cassie, grab those cables, we're gonna have to connect the cradle to the computer in order to upload Jarvis into the synthetic body," Banner said.
******************
"This framework is not compatible," Tony said, tapping away on the computer.
"The genetic coding tower's at 97%. You have got to upload that schematic in the next three minutes."
Cassie moved to stand in front of Bruce as Steve and the Maximoffs walked into lab. "I'm gonna say this once," Steve commanded.
"How 'bout 'nonce'?"
"Shut it down," Cap demanded.
"Nope, not gonna happen," Tony spat back.
"You don't know what you're doing," Steve said.
"And you do? She's not in your head?" Bruce gestured at the witch.
"I know you're angry," she said, walking around to Steve's side.
"Oh, we're way past that. I could choke the life out of you and never change a shade."
"I don't even have to worry about that," Cassie added.
"Banner, after everything that's happened..." Steve started.
"That's nothing compared to what's coming!" Tony shouted.
"You don't know what's in there!" Wanda shouted back.
"This isn't a game!" Rogers shouted.
"The creature..." Wanda began as her twin ran around the lab, destroying and disconnecting everything.
"No, no. Go on. You were saying?" He threw the cables on the ground and looked around the lab.
A bullet came up through the glass, causing Pietro to fall through. Wanda called his name as Cassie looked down the hole at Clint, who stepped on the mutant and smiled. "What? You didn't see that coming?"
The computer beeped at Stark, so he started tapping at the keyboard again. "I'm rerouting the upload." Steve pulled his hand back and threw his shield at the computer and Tony, who blasted him with a repulsor beam and called the rest of his suit.
Banner grabbed Wanda from behind as Cassie moved to grab Steve's shield. "Go ahead, piss me off," Banner urged as Clint ran up the stairs.
Steve jumped at Tony, intent on punching the genius, but flew backwards as another repulsor beam hit him. Tony flew backward, too, as Cassie ran for the computer. "Reroute the upload," she whispered to herself in hopes that she could figure out how to do that. She was never that great with computers. Wanda pulled herself from Banner's arms in the confusion and used her 'magic' to hit him back away from her. Cassie's eyes fell on Thor as he ran into the room and jumped on top of the cradle, calling forth a lightning bolt to hit it. Warning: Power Overload came across the screen in front of her as the upload rapidly finished. The cradle exploded open, sending Thor flying backward and everyone else to shield their eyes.
A look of awe and fear crossed everyone's faces as the red synthetic man jumped out of the cradle and looked around as he stood. He jumped at Thor, who threw him out the lab window to the living area below. He stopped just short of the glass on the outside of the building, flying in front of it and looking out at the city. Thor followed him down, as did Cap and Cassie. Thor put a hand up to stop Steve getting closer. His skin changed from almost completely red to red and green as he turned and flew to stand next to Thor in the living room. "I'm sorry, that was... odd." Jarvis' voice came out of the android. "Thank you," He addressed Thor. As he examined the Asgardian, a yellow cape appeared behind him.
"Thor. You helped create this?" Steve asked.
"I've had a vision. A whirlpool that sucks in all hope of life and at its center is that." Thor pointed to the android's forehead.
"The gem?" Cassie asked, stepping forward.
"It's the Mind Stone, Lady Cassie. It's one of six Infinity Stones. The greatest power in the universe, unparalleled in its destructive capabilities."
"Then, why would you bring it to..."
"Because Stark is right."
"Oh, it's definitely the end times," Banner said, under his breath.
"We were supporting this, remember?" Cassie put her hand on his shoulder.
"The Avengers cannot defeat Ultron," Thor continued.
"Not alone," the android added.
"Why does your 'vision' sound like Jarvis?"
"We... we reconfigured Jarvis' matrix to create something new," Tony answered, walking toward the android.
"I think I've had my fill of new."
"Then, go back to sleep," Cassie responded, earning her a hurt look from the captain.
"You think I'm a child of Ultron," Vision said.
"You're not?"
"I'm not Ultron. I am not Jarvis. I am... I am," he concluded.
"I looked in your head... and saw annihilation," Wanda accused, walking forward.
"Look again."
Clint scoffed. "Yeah. Her seal of approval means jack to me."
"Their powers, the horrors in our heads, Ultron himself, they all came from the Mind Stone. And they're nothing compared to what it can unleash. But with it on our side..." Thor started.
"Is it?" Cassie asked.
"Are you? On our side," Steve clarified.
"I don't think it's that simple," the Vision answered.
"Well, it better get real simple, real soon." Clint threatened.
"I am on the side of life. Ultron isn't. He will end it all."
"What's he waiting for?" Tony asked.
"You."
"Where?" Bruce asked.
"Sokovia," Clint answered. "He's got Nat there, too."
"If we're wrong about you..." Bruce started, walking forward with his hands clasps. "If you're the monster that Ultron made you to be..."
"What will you do?" Vision looked around at the group. The silent 'We will kill you' vibe spoke its words. He started to pace, walking past Banner. "I don't want to kill Ultron. He's unique, and he's in pain. But that pain will roll over the Earth, so he must be destroyed. Every form he's built, every trace of his presence on the 'net. We have to act now. And not one of us can do it without the others. Maybe I am a monster." He looked down at his hands. "I don't think I'd know if I were one. I'm not what you are, and not what you intended. So, there may be no way to make you trust me. But we need to go." He turned, offering Mjolnir to Thor. The Avengers' eyes focused on the hammer and Vision's lack of strain.
"Holy shit." Cassie scoffed as Thor took the hammer and Vision walked away.
"Right," Thor said, before walking up and patting Tony's shoulder. "Well done."
"Three minutes. Get what you need," Steve ordered.
"Yes, boss," Cassie said, running for the elevator.
"You going for guns?" Clint called after her.
"I'm going for anything I can get my hands on," she called back.
KITCHEN SINK TAGS @heyitscam99 @wonderlandfandomkingdom @unlikelysamwinchesteronahunt @mrs-meghan-winchester @henrymorganme @lonely-skys @allykat2108
8 notes
·
View notes
Photo

New Post has been published on https://primorcoin.com/spike-lee-on-using-nfts-to-fund-films-the-horse-is-out-the-barn/
Spike Lee on Using NFTs to Fund Films: 'The Horse Is Out the Barn'

In brief
Director Spike Lee will release a series of Ethereum NFTs based on his appearance as Mars Blackmon in “She’s Gotta Have It.” Lee spoke with Decrypt about how the project will help fund young filmmakers and let NFT holders vote on which projects are made.
Legendary filmmaker Spike Lee is the latest veteran director to make the leap into the NFT space with an upcoming collection of Ethereum artwork based on stills from his 1986 feature, “She’s Gotta Have It.”
Like Quentin Tarantino and Kevin Smith, the “Do the Right Thing” writer and director is exploring the potential to use his own IP in the Web3 space. In this case, he’s doing so through a new filmmaking platform called The Visible Project, which will support young directors and let NFT holders vote on which films get funded.
Lee appeared at Gary Vaynerchuk’s VeeCon conference in Minneapolis on Friday to discuss the initiative, and then spoke with Decrypt after his onstage interview.
The Visible Project will release 3,945 Ethereum NFTs featuring still images of Lee portraying the character Mars Blackmon in “She’s Gotta Have It.” Lee went on to appear as Blackmon in a series of Nike commercials, most notably with Michael Jordan, and Lee recently directed and appeared as Blackmon in a short film to mark Nike’s 50th anniversary.
Each NFT image was rendered from the original 35mm print of the film, plus they feature generative effects, frames, and other details to make each one visually distinct from the rest. They’re set to launch this summer, although final details have yet to be confirmed.
Onstage, Lee told VaynerNFT president Avery Akkineni that his adult children Satchel and Jackson introduced him to NFTs, which serve as a proof of ownership for things like digital artwork, collectibles, and more. He’s been buying single-edition NFT artwork and interacting with artists since then, as well as doing homework to learn about the space.
“I think that to do anything in this world, to come on successful, you have to do some research to learn about it,” Lee told Decrypt. “To just jump into something not knowing anything about it—that’s not a wise move.”
“Maybe I would have done that in my days of ignorance,” he added, noting that he’s 65 years old. “But not now!”

Example images from Spike Lee’s NFT drop. Image: The Visible Project
After such a long and acclaimed filmmaking career, Lee told Decrypt that creating NFTs is “something new for me.” The Visible Project is powered by Habitat Labs, a Web3 infrastructure startup, and Lee said that they’ve “put him in the best position to win.” He then added, “Now it sounds like sports.”
The Visible Project aims to democratize film funding by using NFT drops to raise money, and then allowing token holders to vote on whether or not proposed projects receive funding.
Co-founder Eliot Greene told Decrypt at VeeCon that Lee will mentor filmmakers whose films are funded through The Visible Project, and that they can tap into some of the production resources of Lee’s studio, 40 Acres and a Mule Filmworks. The platform also plans to launch an in-person film festival in Brooklyn in spring 2023, along with a virtual version.
“We’re creating a decentralized film studio, where we’re going to be financing short films directly from emerging creators, and every NFT is a vote,” said Greene. “So we’re democratizing the Hollywood greenlight process where you get to actually say what content you want to see made.”
The Visible Project the latest in a recent string of Web3 initiatives designed to shake up modern filmmaking, ranging from indie creators to beloved veteran directors. Platforms like Roman Coppola’s Decentralized Pictures and Mogul Productions similarly let token holders vote on which projects are made, while FF3 uses NFT drops to raise funds for films.
Meanwhile, Shibuya is a platform that lets NFT buyers influence the direction of a film by voting on story decisions. And Kevin Smith’s upcoming Killroy Was Here NFTs will let owners create their own films and shorts using the characters from their respective NFTs, and then the “Clerks” director will collaborate with them to release anthology-style sequels.
“The horse is out the barn, as they say,” Lee told Decrypt regarding the potential for NFTs to disrupt traditional film financing models.
As for whether he might consider funding his own films via NFTs, Lee said that it would have to be a pretty low-budget independent film. But there’s a benefit to pursuing community funding via decentralized Web3 models.
“The win is: you own it,” he said. “You own it.”
Want to be a crypto expert? Get the best of Decrypt straight to your inbox.

Get the biggest crypto news stories + weekly roundups and more!
Source link
#Blockchain #Crypto #CryptoNews #TraedndingCrypto
0 notes
Text
Egisenc Encrypted File Converter Software For Mac

Disk Utility User Guide
Disk Utility on Mac supports several file system formats:
What is File Extension EGISENC? Egis is the primary software program that utilizes the Egis Encrypted Data file, originally developed by Egis Technology Inc. Internal website statistics show that EGISENC files are most popular with users in United States and those running the Windows 10 operating system.
Egisenc Encrypted File Converter Software For Mac. No upcoming events. Feb 23, 2020 5. Check the 'Encrypt the File Only' box to encrypt the individual file, then click 'OK' to finish. How to Decrypt a File in Windows 10/8/7. Read this part and see how to decrypt PDF and Excel files. If your encrypted files are lost, you can recover deleted data first, and use the ways below to decode. How to Remove Encryption from a PDF File. EGISENC file extension is associated with Egis developed by EgisTec Inc. Egis is bundled with Acer notebook and desktop computers named Acer eDataSecurity Management. It has essential personal data security functions with an easy-to-use and plug-and-play design. Egis helps you to encrypt both files and folders for data security.
Apple File System (APFS): The file system used by macOS 10.13 or later.
Mac OS Extended: The file system used by macOS 10.12 or earlier.
MS-DOS (FAT) and ExFAT: File systems that are compatible with Windows.
Apple File System (APFS)
Apple File System (APFS), the default file system for Mac computers using macOS 10.13 or later, features strong encryption, space sharing, snapshots, fast directory sizing, and improved file system fundamentals. While APFS is optimized for the Flash/SSD storage used in recent Mac computers, it can also be used with older systems with traditional hard disk drives (HDD) and external, direct-attached storage. macOS 10.13 or later supports APFS for both bootable and data volumes.
APFS allocates disk space within a container (partition) on demand. When a single APFS container has multiple volumes, the container’s free space is shared and is automatically allocated to any of the individual volumes as needed. If desired, you can specify reserve and quota sizes for each volume. Each volume uses only part of the overall container, so the available space is the total size of the container, minus the size of all the volumes in the container.
Choose one of the following APFS formats for Mac computers using macOS 10.13 or later.
APFS: Uses the APFS format. Choose this option if you don’t need an encrypted or case-sensitive format.
APFS (Encrypted): Uses the APFS format and encrypts the volume.
APFS (Case-sensitive): Uses the APFS format and is case-sensitive to file and folder names. For example, folders named “Homework” and “HOMEWORK” are two different folders.
APFS (Case-sensitive, Encrypted): Uses the APFS format, is case-sensitive to file and folder names, and encrypts the volume. For example, folders named “Homework” and “HOMEWORK” are two different folders.
You can easily add or delete volumes in APFS containers. Each volume within an APFS container can have its own APFS format—APFS, APFS (Encrypted), APFS (Case-sensitive), or APFS (Case-sensitive, Encrypted).
Mac OS Extended
Choose one of the following Mac OS Extended file system formats for compatibility with Mac computers using macOS 10.12 or earlier.
Mac OS Extended (Journaled): Uses the Mac format (Journaled HFS Plus) to protect the integrity of the hierarchical file system. Choose this option if you don’t need an encrypted or case-sensitive format.
Mac OS Extended (Journaled, Encrypted): Uses the Mac format, requires a password, and encrypts the partition.
Mac OS Extended (Case-sensitive, Journaled): Uses the Mac format and is case-sensitive to folder names. For example, folders named “Homework” and “HOMEWORK” are two different folders.
Mac OS Extended (Case-sensitive, Journaled, Encrypted): Uses the Mac format, is case-sensitive to folder names, requires a password, and encrypts the partition.
Windows-compatible formats
Choose one of the following Windows-compatible file system formats if you are formatting a disk to use with Windows.
MS-DOS (FAT): Use for Windows volumes that are 32 GB or less.
ExFAT: Use for Windows volumes that are over 32 GB.
See alsoPartition schemes available in Disk Utility on MacAbout Disk Utility on Mac

Egisenc Encrypted File Converter Software For Mac Shortcut
Locking your precious files, documents, photos, and other data through encryption is one of the safest ways to protect your personal information where only authorized users can access it. For the same task, Encryption software for Mac users are so reliable and trustworthy that they can save their personal details like bank information, transaction, passwords, etc. without worrying about its breach at all. How? Simply, locking it all with a Master Key.

Why Do I Need Encryption Software?
Have you ever heard about identity theft? Identity theft has become common by hackers around the world to peek-in details like Credit Card number, SSN, Passport number, etc. so as to gain personal or monetary gains.
‘You can know more, become aware of it and its solutions with How To Prevent Identity Theft?’
In the same way, your files, documents, apps, websites, etc. can be noted by onlookers for their personal profits and need a reliable safety lock. And here, encryption software for Mac works thereby locking them all securely and placing a password before. Now no unknown user can open up any file in office or home and your data will remain intact the way it is.
Let’s just go through some of the best Mac security software for this year!
Best Encryption Software For Mac 2021
Audio File Converter Software
1. Cisdem AppCrypt: For Website & Apps Encryption
Cisdem Appcrypt is quite a distinct encryption tool that locks up various apps and websites, primarily. You can also secure your photos, Contacts, Quicken, iTunes, Mail, etc. on your Mac very easily.
Moreover, add those websites that need a blockage in your Mac by placing them on the blacklist. This might be one of the best ways to keep your kids away from accessing porn websites. Every time anyone opens it, a password will be asked which is known only to you.
Other than that, you can also view the number of failed attempts some other user has made to access the blocked content.
Though Cisdem does not lock individual files but definitely the software that opens all those files.
2. VeraCrypt: For File Encryption
Provide your data high-grade protection using VeraCrypt which is considered as potent encryption software for Mac users. Very easy to use and backed up by on-the-fly-encryption or OTEF, it can also encrypt your folder in a customized manner. Yes, you can encrypt a portion of the file or the whole of it, as required.
Interestingly, Veracrypt uses advanced security algorithms that immunes upcoming brute-force attacks in your Mac. You can also add details about your data including volume, size, location, etc. for better customization. This all will let you escape from any data leak or chances of theft, ultimately!
See Also:-
Egisenc Encrypted File Converter Software For Mac Windows 10
The Best Mac Apps & Utilities You Should...Whether you’re a Mac newcomer or seasoned master, this list of Best Mac Apps and Utilities would certainly make your...
3. Concealer
Another Mac security software that uses AES-256 data encryption standard is Concealer! Now you can protect your credit card information, website passwords, software license codes, files, photos and much more by locking it all behind a master key. Apart from hiding data, you can also set up Note Cards as your journal within it.
It also auto-locks your files if your Mac has not been left open for a while. Your files will be organized within the Encryption Software at one end whereas you can assign separate passwords for your files individually, at another.
4. CloudMounter: For Online Data Encryption
Let’s call it one more solid encryption software for Mac, CloudMounter can organize cloud servers and keep them protected with secure passwords. These servers include Dropbox, Google Drive, FTP, FTPS, Amazon S3, etc.
Once the software is in your Mac, choose the file, select ‘Encrypt’ and type a password to verify it. Yes, it’s done! And guess what, this method is also freeing up space on your Mac while adding storage for the future.
5. FileVault: For Mac Disk Encryption
For all the Mac OS x 10.7 and above users, File Vault can act as powerful encryption software where encryption, as well as decryption, are on-the-fly. The software also allows you to prepare a master password for the case when the present one is lost or forgotten.
Its updated version called FileVault 2 protects your hard disk using the standard XTS-AES 128-block cipher that performs quite better than many other algorithms.
You can approach this method by selecting System Preferences > Security & Privacy > File Vault > click on the Lock icon. If there are more than one user accounts in your Mac, each of them has to enter separate passwords for file protection.
Conclusion
All the encryption software for Mac here is quite amazing so as to keep your sensitive information hidden. But if you ask us, in-built FileVault and Concealer are great options to be considered.
Egisenc Encrypted File Converter Software For Mac Os
Though each of them has its own qualities, choose the one that suits your genre aptly. You can also check the best encryption software for Windows here.
Egisenc Encrypted File Converter Software For Mac Windows 7
All your comments and suggestions are welcomed in the section below. And in case you have any queries, send us a buzz! Also, do not forget to keep track of our YouTube and Facebook page for regular Tech-updates.

0 notes
Text
Cryptography 101: How a Symmetric Key Exchange Works (Basically)
Syndicated from Medium
Webster’s dictionary defines cryptography as… I’m just kidding. This blog post is about cryptography, though just an intro.
Just to start somewhere, let’s go over the Diffie-Hellman Public Key encryption method, which uses a symmetric key algorithm. That means that the same cipher is used to encrypt and decrypt a message. In the feature film National Treasure, the cipher on the back of the United States constitution is an example of a symmetric key.*
A lot of digital cryptography is based on what is known as a trapdoor function. The function is difficult to reverse engineer when given just the result of said function. For the purposes of illustration we are just going to use a “door function” (not a real thing). I’m making up that terminology for the purposes of this example. We will pretend that our function is difficult to reverse engineer (but you will see that it is not).
Example trapdoor function (a real thing):
You know there are two numbers that when multiplied, result in 17,078,781,140,149. Without the hint that one of those numbers is 1,766,021, it would be time consuming, if not fairly difficult to determine which two numbers were multiplied to result in 17,078,781,140,149. That ‘hint’ is the trapdoor. (The other number was 9,670,769. With the trapdoor you can divide 17,078,781,140,149 by 1,766,021 and figure that out for yourself).
Example door function (again, not a real thing):
You know there are two numbers that when multiplied, result in 15. No hint is required to determine that the two numbers were 3 and 5. Technically this is still a trapdoor function, we are just calling it a “door function” because it is easy to reverse engineer just by looking at it. Just to repeat, I made up “door function”. I thought it was vaguely humorous and I appreciate whimsy.
I manage to wrap my head around Public Key cryptography like this: multiply a Public Key and a Secret Key to get a common cipher, aka a Shared Secret. Your Public Key and Secret Key are both different than the other person’s Public and Secret Key, but both sets of keys, when multiplied, result in the same shared secret. This is way simplified and the actual math involves Totients and a Modulus but this is Cryptography 101, The Intro Lesson.
Let’s get a cast of characters together to illustrate an example. Meet Ajay, Beyonce, and Christina. Each person’s Public Key is generated by multiplying their Secret Key by 5. Again, in real life, the math in that calculation is sliiiiightly more complicated, but suspend your disbelief with me for then next few paragraphs. It might go without saying but everyone’s Public Key is known by everyone else. It’s public.
Behold, a handy chart to keep it all straight:

Now for the fun part. Ajay writes a message “Hi Beyonce, have you seen the movie Speed?” This message is for Beyonce’s eyes only, so Ajay multiplies his Secret Key by Beyonce’s Public Key and uses the result to encrypt it.
Multiplying those keys results in 75. This is the shared secret between Ajay and Beyonce. For demonstration purposes, our encryption method is to interleave the shared secret between every character of the message, and decryption is removal of all instances of the shared secret. It is quite elementary, but just pretend that on the internet, this makes it impossible to read.
When we apply this totally believable encryption method to the message, this gives:
“H75i75 75B75e75y75o75n75c75e75,75 75h75a75v75e75 75y75o75u75 75s75e75e75n75 75t75h75e75 75m75o75v75i75e75 75S75p75e75e75d75?”
Look at how difficult it is to read now, Internet!
Ajay sends that encrypted message and no one can read it (are you still pretending?!), because they don’t know the shared secret (75). Even if some unnamed nefarious character had Beyonce’s and Ajay’s Public Keys, 25 and 15, neither of these numbers alone help to decrypt the message.
Beyonce receives the message, but due to a Shakespearean misunderstanding, she thinks the message is from Christina. So she uses Christina’s Public Key, 10, with her Secret Key, 5, to decrypt the message. She computes 10 * 5 and gets 50. But when she uses this shared secret and removes all the 50s from the message, it remains encrypted.
Further confusion continues, and now Christina thinks Ajay sent the message to her. Christina uses her Secret Key, 2, and Ajay’s Public Key, 15, to get a shared secret of 30. This too, fails to decrypt the message.
After a bit of hilarity and hijinx, the misunderstanding is resolved. Beyonce knows the message is from Ajay and is intended only for her. She multiplies her Secret Key, 5, and Ajay’s Public Key, 15, to get, wait for it… 75. Their shared secret. Removing all 75s from the message gives:
“Hi Beyonce, have you seen the movie Speed?”
Boom.
Because only Ajay & Beyonce’s shared secret worked to decrypt the message, Beyonce knows for sure that the message was intended for her and that it was sent by Ajay. Ajay “digitally signed” the message because he used his Secret Key.
Needless to say, but I’m saying it anyway, we used easy numbers, easy algorithms (multiplication), and an insanely simplistic “encryption” method. But this is the essence of the Diffie-Hellman Public Key encryption method, symmetric key cipher. Wikipedia has the real math if you are interested.
There are other encryption methods and even other Public Key exchange encryption methods. Search the web for PGP and RSA if you want to venture out of the kiddie pool.
That concludes today’s lesson. Below is optional homework. Be sure to keep an eye out for Cryptography 101, Lesson Two: Asymmetric key algorithms or How to explain coprime numbers succinctly to kindergarteners.
If you would like to play along at home, dear reader, use your browser console to play around with the concept.
The console can be accessed the following ways — Chrome: View > Developer > JavaScript Console Firefox: Tools > Web Developer > Web Console Safari: download Chrome or Firefox Edge: download Chrome or Firefox
And the code…
const ajaysSecretKey = 3 const beyoncesSecretKey = 5 const commonFactor = 5
function createPublicKey(secretKey, commonFactor) {
return secretKey * commonFactor }
function signPublicSecretKey(publicKey, SecretKey) { let commonCypher = publicKey * SecretKey return commonCypher
}
function encryptMsg(message, commonCypher) { let encrypted = Array.from(message).join(commonCypher) console.log(message) console.log(`when encrypted becomes:`) console.log(encrypted) console.log(``) return encrypted }
function decryptMsg(message, commonCypher) { let re = new RegExp(commonCypher,`g`) let decrypted = message.replace(re, ``) console.log(message) console.log(`when decrypted becomes:`) console.log(decrypted) console.log(``) return decrypted }
const ajaysPublicKey = createPublicKey(ajaysSecretKey, commonFactor)
const beyoncesPublicKey = createPublicKey(beyoncesSecretKey, commonFactor)
const sharedSecret = signPublicSecretKey(ajaysPublicKey, beyoncesSecretKey)
console.log(``)
let ajaysMsg = `hi Beyonce, have you seen the movie speed?`
let ajaysEncryptedMsg = encryptMsg(ajaysMsg, sharedSecret) let ajaysDecryptedMsg = decryptMsg(ajaysEncryptedMsg, sharedSecret)
*I have not seen National Treasure so that cipher analogy may not be applicable. I just wanted to soften the topic with a pop culture reference. Did it work?
2 notes
·
View notes
Text
Ransom from Home – How to close the cyber front door to remote working ransomware attacks
Our working routines have shifted dramatically as a result of the Coronavirus. These will, in many circumstances, outlive the pandemic. Working from home, though, comes with its own set of risks. One is that you may be inviting ransomware assaults from a new breed of cybercriminal who has previously focused on directly attacking the business network. Why? Because you're increasingly seen as a soft target if you work from home.—the open doorway to extorting money from your employer.
So, how can ransomware make its way to your front door? What can a stay-at-home worker do to close that door?
The new ransomware trends Trend Micro detected approximately 61 million ransomware-related threats last year, up 10% from the previous year. But things have only worsened since then. Ransomware detections increased by 20% globally in the first half of 2020, reaching 109 percent in the United States. And why is it the case?
Ransomware, at its most basic level, looks for and encrypts most of the data on a targeted machine, rendering them unusable. Victims are then asked to pay a ransom within a certain amount of time in order to acquire the decryption key that will allow them to access their data. If they don't, and this material hasn't been backed up, it could be lost forever.
However, in recent years, attention has shifted to public and private sector firms with employees who work from home (WFH). Remote workers are less likely to be able to defend themselves against ransomware assaults, and they also serve as a convenient stepping stone into high-value corporate networks.Furthermore, cybercriminals are increasingly trying to steal sensitive data before encrypting it, even though they're more likely to get a greater ransom from a remote employee's data than they are from a regular customer, especially if the data is ensured by cyber-insurance.
Homeworkers are being targeted increasingly frequently for a variety of reasons: They may be more easily sidetracked than those at work. The security of your home network and endpoints may not be up to par with that of a business. Home systems (routers, smart home gadgets, PCs, and so on) may be out of date and hence more vulnerable to attacks. Remote workers are more likely to visit vulnerable websites, download dangerous software, or share computers/networks with people who do. Corporate IT security staff may be overburdened with other responsibilities, making it impossible to provide fast assistance to a remote worker. In the past, security awareness initiatives may have been absent, fostering harmful habits among workers at home.
What’s the attack profile of the remote working threat?
In short, the bad guys are now attempting to acquire access to your corporate network via a VPN, or to the cloud-hosted platforms you use for work or file sharing, in order to steal and subsequently encrypt company data with ransomware as widely as possible throughout your firm. The procedures, on the other hand, are well-known.
Attempting to persuade you to engage in risky conduct via email phishing is the standard approach of convincing you to click links that bring you to malicious websites or download a malicious file to begin the infection process.
Before attackers transmit the complete ransomware payload, they steal or guess your log-ins to work email accounts, remote desktop tools (i.e., Microsoft Remote Desktop or RDP), cloud-based storage/networks, and so on. This may be done through a phishing email that is spoofing a legitimate source, or they could check for your use of specific tools and then try to guess your password.A keylogger is integrated into a new Mac malware named EvilQuest. It has the potential to intercept your workplace passwords as you enter them in. It's a two-pronged attack: first, steal the data, then encrypt it.
To leverage home networks as a stepping-stone into your corporate network, exploit weaknesses in smart home devices/routers or their easy-to-guess/crack passwords.
How can I prevent ransomware when working from home? The good news is that you, the remote worker, may take some relatively simple precautions now to help limit the new ransomware's cascading hazards to your firm. Consider the following:
Phishing emails should be avoided at all costs. However, if your employer offers training and awareness classes, take advantage of them. Maintain the newest versions of your home network firmware, PCs, Macs, mobile devices, software, browsers, and operating systems, as well as remote access tools and VPNs (your IT department may do some of this remotely). Use an up-to-date network and endpoint antivirus from a trusted provider to safeguard your home network, PCs, and mobile devices. (Anti-intrusion, anti-web threat, anti-spam, anti-phishing, and, of course, anti-ransomware elements should all be included in the solutions.)
If multi-factor authentication (MFA) is used, make sure that remote access tools and user accounts are protected, and that remote access to your home router is not possible. Disable Microsoft macros if at all possible. They're a common method of attack. Back up important files using the 3-2-1 rule on a regular basis.
How Trend Micro can help To summaries, to keep your home network and all endpoints (laptops, PCs, and mobile devices) safe from ransomware, you must safeguard your home network and all endpoints (laptops, PCs, and mobile devices). Trend Micro can assist you with this.
On desktop PCs, Trend Micro Maximum Security offers powerful protection against ransomware-related attacks. It includes Folder Shield, which protects essential data from ransomware encryption and allows it to be stored locally or synced to cloud services such as Dropbox®, Google Drive®, and Microsoft® OneDrive/OneDrive for Business.
Mobile endpoints: Trend Micro Mobile Security (also included in TMS) guards against ransomware on Android and iOS smartphones.
Secure passwords: Trend Micro Password Manager allows users to securely save and recall strong, unique passwords across numerous devices for all of their apps, websites, and online accounts.
You, the remote worker, may help close the front door to ransomware by using these solutions to safeguard your work, devices, and company from data theft and ransomware encryption.
Source:https://cyber-security-information.blogspot.com/2021/08/ransom-from-home-how-to-close-cyber.html
0 notes
Text
Why choose the services of 24×7 assignment help?
In the above fundamental securities, the algorithms to be learned for making a digital data secure is not an easy task for a student. The homework and assignment may make them feel confused with algorithms and other cryptography aspects. Where our https://www.allhomeworkassignments.com/ cryptography assignment assistance will surely be helpful to you. There are symmetric and asymmetric algorithms and also encryption and decryption which are the basis of the cryptography. They need to give special attention towards this topic of programming as a single wrong code can affect the security algorithms. Taking online help from https://www.allhomeworkassignments.com/ is always useful.
Why choose the services of 24×7 assignment help?
When you are in search of an online expert to ask them to do my cryptography homework and assignment then https://www.programmingonlinehelp.com/ are one among the other online companies by providing efficient services that too at affordable cost. Let us see what our strengths are and how we are good for solving your assignments?
•You get content which will be only yours that is unique and plagiarism free. How to solve cryptography assignments? Is not a big question for our https://www.programmingonlinehelp.com/ experts. They have complete knowledge to give the needed help with all types of question, You get the help from the experts that are dedicated to their work and always give you timely delivery. You can ask for do my nursing cryptography at any time as we provide a service which is available 24/7 for you. You may be around anywhere in the world you just need to go online and hire https://www.programmingonlinehelp.com/ experts through simple steps and also make the payments with secure methods. You be assured with our work that it will be without errors and it will make a huge difference in your grades at all time.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Note
Me trying to decrypt the code even though I failed math and the most advanced computer science course I took was HTML coding on Codeacademy:

Nudges paper to the team in charge of the zodiac killer case. “Can you guys help me with my homework?”
yo have you seen the tva's tumblr page?? its very strange
well i have now and it is very cryptic
49 notes
·
View notes
Text
CSE445/598 Project 2 (Assignments 3 and 4) – Solved
Introduction
The purpose of this project is to make sure that you understand and are familiar with the concepts covered in the lectures, including distributed computing, multithreading, thread definition, creation, management, synchronization, cooperation, event-driven programming, client and server architecture, service execution model of creating a new thread for each request, the performance of parallel computing, and the impact of multi-core processors to multithreading programs with complex coordination and cooperation. Furthermore, you are able to apply these concepts in a programming project. You can choose to do this project as an individual project or as a team project of two or three members. In the case of the team project, a declaration must be given at the end of the assignment, which identifies the parts of individual contributions and team efforts. An overall percentage of contribution of each member (e.g., 50% and 50%, or 30%, 35% and 35%) must be given, which will be used as a reference of assigning (scaling) grades. Only one copy of the project should be submitted by one of the team members. A team-building document is given separately for assignments 3 and 5. We need to know the teams in advance, because we need to create a server site for each team.
Section I Preparation and Practice Exercises (No submission required)
No submission is required for this section of exercises. However, doing these exercises can help you better understand the concepts and thus help you in quizzes, exams, as well as the assignment questions. Reading: Textbook Chapter 2. Answer the multiple choice questions in text section 2.8. Studying the material covered in these questions can help you prepare for the lecture exercises, quizzes, and the exams. Study for the questions 2 through 20 in text section 2.8. Make sure that you understand these questions and can briefly answer these questions. Study the material covered in these questions can help you prepare for the exams and understand the homework assignment. Test the programs given in questions 24 and 25 in text section 2.8. Identify the problems in the program and give correct versions of the programs. If you want solve a more challenging problem in multithreading, you can do question 26 in text section 2.8. Tutorial. To help you complete the project in Section II, you may want go through the tutorial given in the textbook chapter 2, which consists of Reading the case study in text section 2.6.3. Implementing and testing the program given in the case study. The program can be used as the starting point for your project in Section II. Extending the program based on the requirement in Section II.
Section II Project (Submission required)
Warning: This is a long programming project designed for a study load for three weeks of estimated 3*8 = 24 hours. It is challenging at both the conceptual level and the implementation level. You must distribute the load in the given three weeks. You will not have enough time to complete it if you start the project only in the last week before the project is due. Purpose of this project is to exercise the concepts learned in this chapter. It is not the purpose of this project to create realistic services and applications. We will create more realistic services and applications in the subsequent projects. In this project, you can use a console application or a simple GUI application to implement the user interface to your program. You do not need to create Web applications. Description: Consider that you are creating an e-business: a book distribution system that involves bookstores and publishers. The system consists of multiple bookstores (clients) and multiple publishers (servers). The bookstores can buy in quantity of books from the publishers with lower prices. The required architecture and the major components of the system are shown in the diagram below.
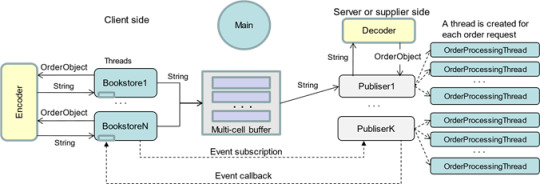
Figure 1 Architecture of a book distribution system In this project, you will implement both clients and servers in one system in multithreading. You will further implement such systems in distributed web client and server systems in the following projects. An Operation Scenario of the book distribution system is outlined as follows: A Publisher uses a pricing model to calculate dynamically the book price for the bookstores. If the new price is lower than the previous price, it emits a (promotional) event and calls the event handlers in the bookstores that have subscribed to the event. A BookStore evaluates the price, generates an OrderObject (consisting of multiple values), and sends the order to the Encoder to convert the order object into a plain string. The Encoder converts the object into a string. The Encoder sends the encoded string back to the caller. The BookStore sends the encoded string to one of the free cells in the MultiCellBuffer. The Publisher receives the encoded string from the MultiCellBuffer and sends the string to the Decoder for decoding. The Decoder sends the OrderObject to the Publisher. The decoded object must contain the same values generated by the BookStore. The Publisher creates a new thread, an OrderProcessingThread, to process the order; The OrderProcessingThread processes the order, e.g., checks the credit card number and calculates the total amount. The OrderProcessingThread sends a confirmation to the bookstore and prints the order (on screen). Note, the encoder and decoder here do not perform encryption and decryption tasks. Components in the diagram are explained in details as follows, with their grading scores (points) allocation, Components 1, 2, 3, 4, and 5 belong to Assignment 3, and the rest of the components belong to Assignment 4. You will submit both assignments together as a project. We will enter the scores under assignments 1 and 2, for the purpose of score management.
Assignment 3 Tasks
Publisher1 through PublisherK* are the objects of a class on the server side: Each object has a method to be started as a thread by the Main method and will perform a number of functions. It uses a PricingModel to determine the book prices. It defines a price-cut event that can emit an event and call the event handlers in the BookStore if there is a price-cut according to the PricingModel. It receives the orders (in a string) from the MultiCellBuffer. It calls the Decoder to convert the string into the order object. For each order, you must start a new thread (resulting in multiple threads for processing multiple orders) from OrderProcessing class (or method) to process the order based on the current price. There is a counter p in the Publisher. After p (e.g., p = 20) price cuts have been made, a Publisher thread will terminate. The bookstores do not have to make an order after each price cut. *Note 1: For the individual project, the number of publishers K = 1. For a group project (both twomember and three-member group), K = 2 if you have a 2-member team, and K = 3 if you have a 3member team. PricingModel: It can be a class or a method in the Publisher class. It decides the price of books, which must be between 50 and 200. It can increase or decrease the price. You must define a mathematical model. The model can be a simple random function for individual projects. However, for the group projects, a more complex model must be developed, where the price must be a function with multiple parameters, such as the available number of the books and the number of orders received within a given time period. In other words, the function must take the amount of orders as input. You can use a hardcoded table of the prices, for example, in each weekday. You must make sure that your model will allow the price to go up some times and go down other times within your iterations of testing. OrderProcessing is a class or a method in a class on the server’s side. Whenever an order needs to be processed, a new thread is instantiated from this class (or method) to process the order. It will check the validity of the credit card number. If you are doing an individual project or a two-member group project, you can define your credit card format, for example, the credit card number from the bookstores must be a number registered to the Publisher, or a number between two given numbers (e.g., between 5000 and 7000). For the three-member group project, a bank service must be created. Each OrderProcessing thread will calculate the total amount of charge, e.g., unitPrice*NoOfBooks + Tax + LocationCharge. For the group (two and three members) projects, a confirmation must be sent back to the bookstore when an order is completed. You can implement the confirmation in different ways. For example, you can use another buffer for the confirmation, where you can use a buffer cell for each thread, so that you do not have to consider the conflict among the threads. However, you still need to coordinate the write and read between the producer and the consumer. BookStore1 through BookStoreN, You can set N = 5 in your implementation. Each bookstore is a thread instantiated from the same class (or the same method in a class). The bookstore’s actions are eventdriven. Each bookstore contains a callback method (event handler) for the Publisher to call when a pricecut event occurs. The bookstore will calculate the number of books to order, for example, based on the need and the difference between the previous price and the current price. The thread will terminate after the Publisher thread has terminated. Each order is an OrderClass object. The object is sent to the Encoder for encoding. The encoded string is sent back to the bookstore. Then, the bookstore will send the order in string format to the MultiCellBuffer. For group project, before sending the order to the MultiCellBuffer, a time stamp must be saved. When the confirmation of order completion is received, the time of the order will be calculated and saved (or printed). The following components will be counted as assignment 3 tasks. OrderClass is a class that contains at least the following private data members: senderId: the identity of the sender, you can use thread name or thread id. cardNo: an integer that represents a credit card number. receiverID: the identity of the receiver, you can use thread name or a unique name defined for a publisher. If you are doing an individual project, you do not need this field. amount: an integer that represents the number of books to order. unit price: a double that represents the unit price of the book received from the publisher. You must use public methods to set and get the private data members. You must decide if these methods need to be synchronized. The instances created from this class are of the OrderObject.
Assignment 4 Tasks
MultiCellBuffer class is used for the communication between the bookstores (clients) and the publishers (servers): This class has n data cells (for individual project, n = 2 and for group project, n = 3). The number of cells available must be less than ( Read the full article
0 notes
Text
War Games - Crypto
As mentioned in previous slides, we will be given homework(s) every week that are sort of flexible, self-learn and self-paced
This week, one of the tasks is to understand and solve a crypto challenges. This is from NSA App and this is a non-NSA alternative LINK.

The next part is my analysis and how I get to solve this puzzle
I first consider the frequency given. B is seem to be the highest frequency letter, so based on ETAOIN, I first assume B to be E. Next for the single letter word O, I guessed it to be A or I since.
match frequency with frequency in english dictionary
Put B as E
G, A, I, O do not not match T since it will not make a make sense word
Single letter words: a or I?
double letter words: as, if, at?
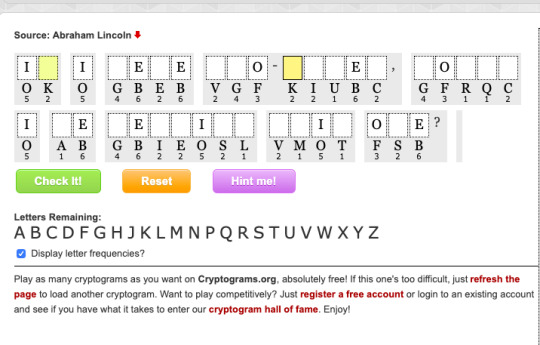
After this, I try to guess and match based on ETAOIN. T does not seem to appear frequently here so I go next to A, O and I. Then I can deduce that S is N which give the word “One?” at the back. I can also guess that G is W and E is R to give the third word a “WERE”
After a few tries, I am able to figure out the secret message!
Reflection: This does looks difficult since this is my first time decrypting a crypto puzzle. But overall I should learn that doing it step by step would give me clues and I shouldn’t get frustrated from the start first. Frequency is also a big help :)
0 notes
Text
Week 7 Homework
I’ve done most of the weekly homework but since I’m doing COMP2511 and the assignment was due last week (pretty bad this term because of the trimesters and also they compressed a four people’s project into two) so I couldn’t do the homework for last week and also some of the module exercises from week 6. I’ve prioritised the lectures, case studies and something awesome projects, but I prioritised the assignment over the homework and module exercises so I’m catching up this week.
Vulnerabilities
Simple Vanilla Cake:
How much of every ingredient to add isn’t given, temperature might be a bit too low.
Caramel Slice:
Again, missing quantities for the ingredients to add
Cheese Souffle:
The time mentioned isn’t maintained properly
Codes:
Length is signed value which means a very large negative number will be smaller than max
Size of isn’t used properly. It will return the sizeof the pointer
Comparing f and sizeof(mybuff), f of type short which is 2 bytes while sizeof returns a long.
OWASP Top 10: Sensitive Data Exposure
Let us consider ourselves as executives at a bank as an example. We have a bunch of users and we need to protect user information to make sure we don’t incur losses if revealed. We do it by hiding information that only we know how to retrieve, kind of like how we hide our personal documents. We need to alter the data and only we should be able to get back the data. We need to do something called encryption. Lets take an account for user ‘Bob’. We can encrypt his name to ‘cpc’ (we shifted each letter by one alphabet called a Caesar cipher). Although this can hide his name, if anyone figures out the pattern he/she will be able to decrypt and find the data which is why we need something stronger. If we do not properly hide or encrypt our user information we might end up revealing sensitive data which is one of the top 10 biggest security vulnerability according to OWASP.
One-Time Pads:
I’ve replicated the Cribb Dragging method using a python script (check out hex()) and XOR the letters each (C1⊕C2=(P1⊕K)⊕(P2⊕K)=P1⊕(K⊕K)⊕P2=P1⊕0⊕P2=P1⊕P2) and obtain the messages
The secret to winning Eurovision is excellent hair
Everyone deserves a hippopotamus when they’re sad
Can you please help Oliver find the flux capacitor
The most important person in the world is me myself
The price of bitcoin is too damn high given the data
0 notes